Smart contracts are now the backbone of decentralized applications (dApps), providing automated, self-executing agreements that eliminate the need for intermediaries. With the rise of blockchain technology, these contracts have gained significant traction, especially in industries like finance, supply chain, and real estate.
These self-executing contracts, written in code, offer unparalleled transparency and immutability. However, the very nature of smart contracts, with their complex logic and reliance on public blockchains, makes them susceptible to various security vulnerabilities.
The consequences of smart contract vulnerabilities can be severe. Exploits can lead to substantial financial losses, damage to the reputation of projects, and erosion of user trust. To ensure the robustness and integrity of DApps, it is imperative to employ robust security measures to mitigate these risks.
| What are Smart Contracts? A smart contract is a program that automatically enforces the terms of an agreement when certain conditions are met. Built on blockchain platforms like Ethereum, these contracts are immutable and decentralized, meaning they cannot be altered once deployed, and no single entity controls them. This immutability ensures trust in the system but also poses challenges: if a bug or vulnerability exists in the code, it can be exploited, and there’s no way to reverse the consequences. |
Recommended Read: Building the Blocks: An Introduction to Smart Contract Development
The Importance of Smart Contract Security: Lessons Learned from Past Exploits
The decentralized nature of smart contracts means that they operate without a central authority. While this reduces the risk of manipulation, it also places the onus of security squarely on the contract’s code. A single vulnerability can lead to the loss of millions of dollars, as evidenced by several high-profile incidents.
The DAO Hack (2016): The Decentralized Autonomous Organization (DAO) was one of the earliest and most ambitious projects on the Ethereum blockchain. However, a reentrancy vulnerability in the DAO’s smart contract code allowed an attacker to drain $60 million worth of Ether. The incident led to a hard fork in the Ethereum blockchain, creating Ethereum (ETH) and Ethereum Classic (ETC). The key lesson from this event is the importance of thorough testing and the risks associated with complex smart contract logic.
Parity Wallet Freeze (2017): The Parity multi-signature wallet was widely used for managing large sums of Ether. However, a flaw in the wallet’s code allowed an attacker to accidentally trigger a function that froze over $150 million worth of Ether. This incident underscores the need for careful design and review of smart contracts, especially those managing significant assets.
The $31 Million Ethereum Theft (2017): In July 2017, an attacker exploited a vulnerability in the Parity wallet’s code, stealing $31 million worth of Ether. The vulnerability was related to how the wallet’s library contract was deployed, highlighting the dangers of code reuse without proper auditing and the need for secure development practices.
Common Vulnerabilities in Smart Contracts
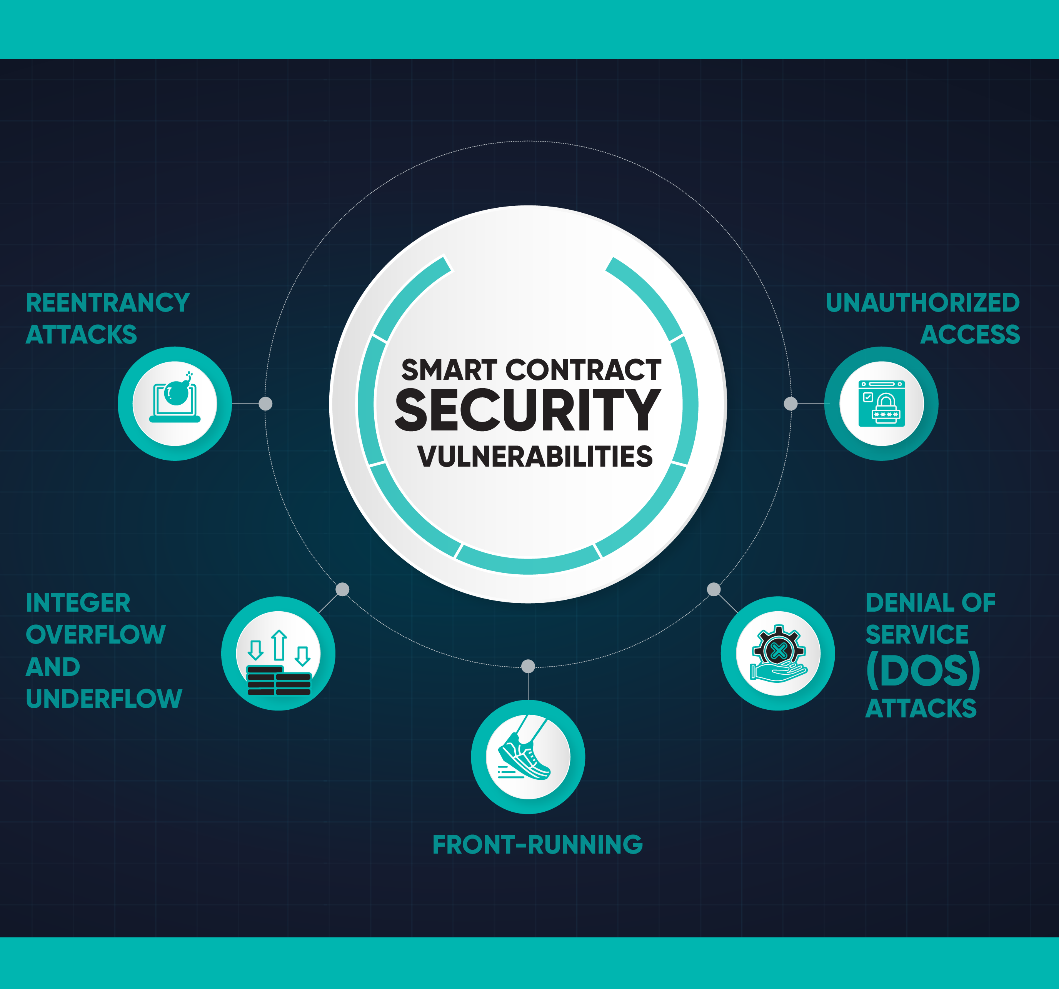
Understanding the common vulnerabilities in smart contracts is the first step toward mitigating risks. Some of the most prevalent issues include:
Reentrancy Attacks: This occurs when a function in a smart contract makes an external call to another contract before resolving its own state. If the external contract is malicious, it can repeatedly call back into the original contract before the first invocation is completed, leading to unexpected outcomes.
Integer Overflow and Underflow: In programming, an integer overflow occurs when a value exceeds the maximum limit that can be stored in a variable, while underflow happens when it goes below the minimum limit. In smart contracts, this can lead to incorrect calculations, allowing attackers to manipulate values in their favor.
Front-Running: In blockchain networks, transactions are processed in the order they are received. Front-running occurs when an attacker notices a pending transaction and submits a similar transaction with a higher gas fee, ensuring it is processed first. This can lead to financial losses for the original transaction initiator.
Denial of Service (DoS) Attacks: A DoS attack in smart contracts can occur when an attacker exploits the limitations in the contract’s code to make it unusable. For instance, an attacker could cause a contract to run out of gas, preventing it from executing further transactions.
Unauthorized Access: Smart contracts often manage sensitive data or assets, and unauthorized access can have severe consequences. This can occur due to weak access control mechanisms or poorly designed permission structures.
Mitigating Smart Contract Vulnerabilities
Mitigating vulnerabilities in smart contracts is essential to ensuring their security, reliability, and trustworthiness. Given the irreversible nature of blockchain transactions, once a vulnerability is exploited, the damage is often irreversible.
Therefore, developers must employ a comprehensive approach that includes secure coding practices, rigorous testing, and continuous monitoring. Here’s a detailed exploration of the strategies to mitigate smart contract vulnerabilities:
1. Adopt Secure Coding Practices
Principle of Least Privilege: This principle dictates that each part of the smart contract should have only the permissions necessary to perform its tasks. By minimizing permissions, the potential impact of a compromised function or contract is reduced.
Modularity and Reusability: Writing modular code with reusable components can help isolate potential vulnerabilities. However, reusing code should be approached cautiously, ensuring that any reused components are thoroughly audited and tested.
Follow Established Standards: Using widely accepted standards, such as the ERC-20 or ERC-721 tokens on Ethereum, can reduce the risk of introducing new vulnerabilities. These standards have been scrutinized by the community, making them more secure.
Avoid Complex Logic: The more complex a smart contract, the higher the likelihood of bugs and vulnerabilities. Simplify logic where possible, making the contract easier to audit, maintain, and understand.
2. Conduct Thorough Audits
Internal Audits: Internal code reviews are the first line of defense. Developers should carefully inspect their code for potential vulnerabilities, using both manual and automated tools. Internal audits can catch many issues before the contract is deployed.
External Audits: Given the high stakes involved, external audits by specialized third-party firms are crucial. These auditors bring a fresh perspective and often have experience identifying vulnerabilities that internal teams might overlook. Multiple audits from different firms can provide added security.
3. Implement Formal Verification
Formal verification involves creating mathematical proofs to ensure that a smart contract behaves as intended under all possible conditions. This approach is particularly effective for high-value contracts where security is paramount. Though complex and time-consuming, formal verification offers a high level of confidence in the contract’s security.
4. Use Testing Tools
Static Analysis: Tools like Mythril, Slither, and Oyente can analyze the smart contract’s source code without executing it. These tools scan for common vulnerabilities, such as reentrancy, unhandled exceptions, and integer overflows, providing a report of potential issues.
Dynamic Analysis: Dynamic analysis tools, such as Echidna and Manticore, simulate contract execution in a controlled environment, testing how the contract behaves under different conditions. This can help identify vulnerabilities that might not be apparent through static analysis alone.
5. Deploy Multisignature Wallets
Multisignature (multisig) wallets require multiple parties to approve a transaction before it can be executed. This adds a layer of security, ensuring that a single compromised private key cannot lead to unauthorized transactions. Multisig wallets are especially useful for managing high-value assets or funds in decentralized organizations.

6. Implement Timelocks
A timelock is a mechanism that delays the execution of certain functions in a smart contract. This delay provides an opportunity to detect and respond to potential vulnerabilities before they can be exploited. Timelocks are particularly useful in governance contracts, where changes to critical parameters or functions can be delayed to allow for community review.
7. Incorporate a Kill Switch
A kill switch is a function that allows developers to halt a smart contract’s operation in case of an emergency, such as the discovery of a critical vulnerability. While this feature can contradict the decentralized nature of smart contracts, it provides a valuable safety net, allowing developers to prevent further damage in the event of an exploit.
8. Regularly Update and Monitor Contracts
Continuous Monitoring: Security is an ongoing process, not a one-time event. Regularly monitoring smart contracts for unusual activity or potential vulnerabilities is essential. Developers should stay informed about new security threats and updates in the blockchain ecosystem.
Upgradeable Contracts: In some cases, developers may opt to use upgradeable contracts, which allow for modifications and patches without requiring the redeployment of the entire contract. However, this approach introduces its own risks and must be implemented carefully to avoid introducing new vulnerabilities.
(Read more here: High-Frequency Trading (HFT) in the Crypto Market: Opportunities and Risks)
9. Community Involvement and Open-Source Contributions
Leveraging the Community: The open-source nature of most blockchain projects allows the community to play a vital role in securing smart contracts. Developers should actively engage with the community by contributing to open-source projects, participating in code reviews, and sharing best practices.
Bug Bounties: Offering bug bounties is an effective way to incentivize security researchers to find and report vulnerabilities in smart contracts. Successful bug bounty programs can identify and mitigate vulnerabilities before they can be exploited by malicious actors.
Looking ahead, advancements in automated security tools, machine learning, and cryptographic techniques like zero-knowledge proofs promise to further bolster the security of smart contracts. However, it is crucial to remain vigilant and proactive in addressing the evolving threats in this space.
Interested to learn more?
At Kenson Investments, we are your dedicated digital asset specialists, committed to delivering top-tier solutions tailored to your needs. Whether you’re navigating the complexities of blockchain investments or seeking strategies to minimize associated risks within your digital portfolio, our team is here to provide the support you need.
Reach out to our digital asset specialists for updates on trends, security tips, and gain insight. Download Kenson Investments’ app now to leverage goal-based planning tools and take control of your financial future today!
Disclaimer: The information provided on this page is for educational and informational purposes only and should not be construed as financial advice. Crypto currency assets involve inherent risks, and past performance is not indicative of future results. Always conduct thorough research and consult with a qualified financial advisor before making investment decisions.
“The crypto currency and digital asset space is an emerging asset class that has not yet been regulated by the SEC and US Federal Government. None of the information provided by Kenson LLC should be considered as financial investment advice. Please consult your Registered Financial Advisor for guidance. Kenson LLC does not offer any products regulated by the SEC including, equities, registered securities, ETFs, stocks, bonds, or equivalents”