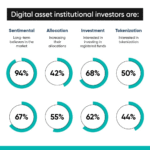
Executive Summary
The rapid advancement of quantum computing presents a significant challenge to the security of digital assets and blockchain technology. Current cryptographic methods, including widely used encryption schemes like RSA, ECDSA, and SHA-256, are built on mathematical problems that classical computers struggle to solve. However, with quantum computing’s superior processing power, these cryptographic safeguards could be rendered obsolete, exposing cryptocurrencies, smart contracts, and decentralized finance (DeFi) platforms to unprecedented vulnerabilities.
This white paper explores the looming threat of quantum computing to blockchain security and highlights the emergence of quantum-resistant cryptography as a critical solution for safeguarding digital assets. Governments, research institutions, and technology companies are already working to develop post-quantum cryptographic (PQC) algorithms, ensuring long-term security for financial systems. Regulatory bodies and blockchain networks are also taking steps to prepare for a quantum-secure future, recognizing the need for proactive adaptation.
Key Insights from This White Paper:
- Quantum Threat to Cryptography:Shor’s algorithm enables quantum computers to break RSA and ECDSA encryption, posing a major risk to blockchain security.
- Emergence of Post-Quantum Cryptography:Research into lattice-based, hash-based, and multivariate polynomial cryptographic techniques offers a promising pathway toward secure blockchain encryption.
- Industry Readiness:Institutions like NIST (National Institute of Standards and Technology) and ISO (International Organization for Standardization) are leading efforts to standardize quantum-resistant encryption.
- Impact on Digital Assets:Crypto investment companies, blockchain asset investments consultants, and digital asset strategy consulting firms must evaluate risk exposure and develop quantum-resistant frameworks to protect investors.
- Future of DeFi and Institutional Adoption:Transitioning to quantum-safe blockchain systems will require coordinated efforts from portfolio management consultants and digital asset management services.
As blockchain technology continues to evolve, staying ahead of cryptographic advancements is crucial. Forward-thinking organizations, including global digital asset consulting firms and real-world asset consultants, must assess their security frameworks and prepare for the quantum era to protect digital assets and maintain trust in decentralized ecosystems.
Introduction: Why Quantum Computing Poses a Threat to Cryptographic Standards
As blockchain technology and digital assets become integral to global finance, ensuring their long-term security is paramount. Cryptographic protocols such as RSA, Elliptic Curve Digital Signature Algorithm (ECDSA), and SHA-256 serve as the foundation for securing transactions, smart contracts, and decentralized finance (DeFi) platforms. However, with the rise of quantum computing, these encryption methods face an existential threat.
Unlike classical computers, which process information using binary bits (0s and 1s), quantum computers leverage quantum bits (qubits), allowing them to perform complex calculations exponentially faster. This capability could enable quantum computers to break encryption methods that are currently deemed secure, exposing blockchain networks to risks such as unauthorized transactions, private key theft, and widespread system vulnerabilities.
The Growing Quantum Threat to Blockchain Security
Blockchain networks rely on asymmetric cryptography, where a public key is used for encryption and a private key is required for decryption. The security of this system depends on the infeasibility of solving complex mathematical problems, such as factoring large prime numbers (RSA encryption) or computing discrete logarithms (ECDSA).
However, quantum computers could break these encryption methods through:
- Shor’s Algorithm:Developed by Peter Shor in 1994, this quantum algorithm can efficiently factor large prime numbers, making RSA and ECDSA-based encryption vulnerable. If a sufficiently powerful quantum computer is developed, it could compute private keys from public keys, effectively compromising digital assets.
- Grover’s Algorithm:This algorithm accelerates the search process for hash functions, reducing the security strength of SHA-256 by half. While this may not render SHA-256 completely useless, it weakens blockchain integrity and necessitates stronger cryptographic measures.
A study published by the University of Sussex in 2022 estimated that a 13 million-qubit quantum computer could break Bitcoin’s encryption within 24 hours, posing an immediate risk to long-term blockchain security. While current quantum computers are not yet at this scale, progress in quantum research indicates that quantum attacks on cryptographic standards may be possible within the next 10 to 15 years.
The Urgency of Preparing for a Quantum-Secure Future
The financial sector, including cryptocurrency investment consultants, digital asset management companies, and DeFi finance consulting services, must proactively prepare for quantum advancements. Blockchain networks that fail to transition to quantum-resistant cryptography risk exposing digital assets to attacks, potentially leading to loss of funds, regulatory challenges, and diminished investor confidence.
Industry leaders, including Security tokens investment consultants and real world DeFi investment consultants, must assess their current encryption models and consider migrating to post-quantum cryptographic (PQC) algorithms before quantum computing reaches maturity.
Quantum Computing: Basics and Differences from Classical Computing
To understand why quantum computing poses a threat to cryptographic security, it is essential to grasp how it differs from classical computing. While classical computers use binary bits (0s and 1s) to process information, quantum computers leverage quantum bits (qubits), which allow them to perform complex calculations exponentially faster. This difference is the foundation of quantum computing’s ability to break widely used encryption protocols.
Key Concepts in Quantum Computing
Quantum computing represents a paradigm shift in computational power, leveraging the principles of quantum mechanics to outperform classical computers in specific tasks. Unlike traditional computing, which relies on binary bits (0s and 1s), quantum computing introduces unique properties such as qubits, superposition, entanglement, and quantum algorithms, all of which contribute to its unprecedented processing capabilities.
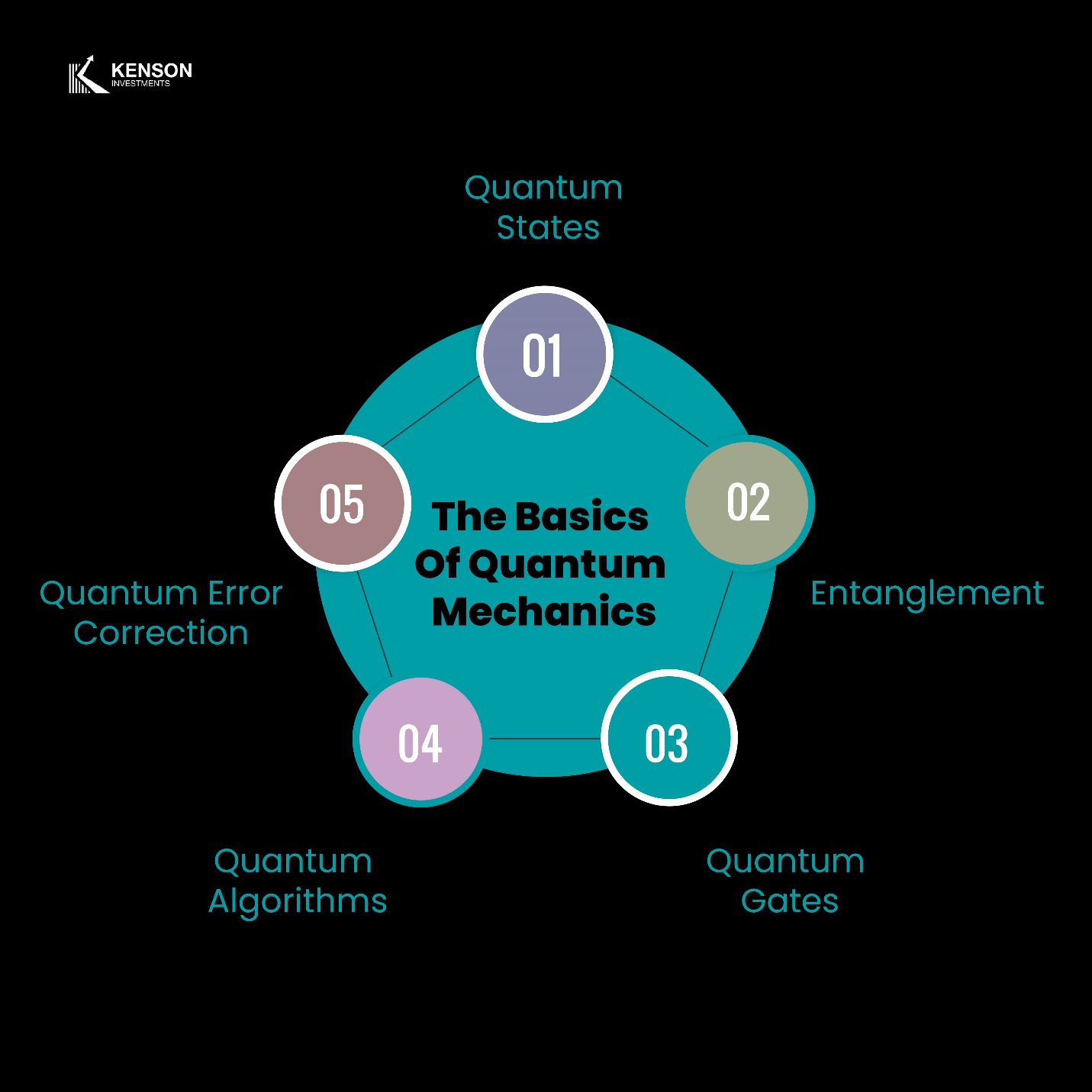
Qubits: The Building Blocks of Quantum Computing
Qubits (quantum bits) serve as the fundamental units of quantum computation. While classical bits can only exist in a binary state (either 0 or 1), qubits take advantage of superposition, allowing them to exist in both states simultaneously. This ability enables quantum computers to perform calculations on multiple possibilities at once, dramatically increasing computational speed and efficiency.
How Qubits Enhance Computational Power
- A single classical bit can represent one of two possible states (0 or 1).
- A 2-bit classical system can represent one of four possible states (00, 01, 10, 11) at a time.
- In contrast, 2 qubits in superposition can represent all four states simultaneously.
- A quantum system with n qubits can exist in 2ⁿ simultaneous states, meaning it can process exponentially more information than a classical system of the same size.
For example, while a classical computer would have to test each possible key one by one when attempting to break encryption, a quantum computer could process multiple keys in parallel, drastically reducing the time required for decryption.
Potential Impact on Cryptography
The power of qubits poses a significant challenge for modern cryptographic standards. Many encryption schemes rely on the assumption that certain mathematical problems take an impractically long time to solve using classical computers. However, quantum computers, by leveraging qubits, could crack encryption protocols that were previously considered secure, necessitating the development of quantum-resistant cryptographic methods.
Superposition: Enabling Parallel Processing
Superposition is one of the defining properties of quantum mechanics and is key to quantum computing’s power. It allows qubits to exist in multiple states at once, significantly enhancing computational capabilities compared to classical systems.
Understanding Superposition in Quantum Computing
- A classical processor with n bits can only store and process one of 2ⁿ possible states at a time.
- A quantum processor with n qubits can store and process all 2ⁿ states simultaneously due to superposition.
This means that a quantum computer with just 300 qubits could theoretically perform more calculations at once than there are atoms in the observable universe (~10⁸⁰ atoms).
Real-World Cryptographic Implications
- Breaking RSA Encryption:Superposition allows quantum computers to analyze and test many potential encryption keys simultaneously, making them much faster at solving cryptographic problems.
- Simulating Complex Systems:This property is particularly useful in fields like cryptography, materials science, and artificial intelligence, where it enables the simulation of highly complex systems that classical computers struggle to handle.
Given the disruptive potential of superposition, digital asset consulting for startups, crypto investment firms, and digital asset portfolio management specialists are actively exploring ways to develop quantum-resistant cryptographic techniques to safeguard decentralized finance (DeFi) and blockchain networks.
Entanglement: Instantaneous Information Sharing
Quantum entanglement is a phenomenon where two or more qubits become intrinsically linked, such that the state of one qubit instantly determines the state of the other—regardless of the distance between them. This interconnectedness has profound implications for information transfer and computational efficiency.
Key Features of Quantum Entanglement
- Instantaneous Correlation:When two qubits are entangled, a change in the state of one qubit immediately affects the other, even if they are separated by millions of light-years.
- Faster Information Processing:Classical communication is bound by the speed of light, but quantum entanglement enables instantaneous state updates, making it useful for ultra-secure quantum communication and decentralized networks.
- Potential for Quantum Internet:Future quantum networks could leverage entanglement to transmit secure information instantly across vast distances.
Security Implications for Blockchain and Cryptography
Quantum entanglement has the potential to revolutionize cybersecurity by enabling quantum key distribution (QKD), which uses entangled particles to create unbreakable encryption keys. However, entanglement also poses risks:
- If a malicious actor harnesses quantum entanglement to break cryptographic security protocols, blockchain networks and encrypted assets could be compromised.
- Cryptographic solutions being explored by RWA DeFi investment consultants, digital asset investment solutions providers, and blockchain asset consulting firms include post-quantum cryptography (PQC) and lattice-based encryption to defend against quantum-enabled attacks.
Quantum Speedup with Algorithms
Quantum computers do not just rely on raw processing power; they also utilize specialized algorithms to solve problems much more efficiently than classical computers. Two of the most important quantum algorithms in the context of cryptography are:
Shor’s Algorithm: A Threat to Modern Encryption
Developed by mathematician Peter Shor in 1994, this algorithm is specifically designed to factor large numbers exponentially faster than classical methods.
Why It Matters:
- Many encryption schemes, including RSA, ECDSA, and Diffie-Hellman, rely on the difficulty of prime factorization to ensure security.
- Classical computers require thousands of years to break a 2048-bit RSA key, but a sufficiently powerful quantum computer running Shor’s Algorithm could achieve this in hours or even minutes.
Impact on Blockchain Security:
- Bitcoin, Ethereum, and other blockchain networks that use ECDSA for digital signatures could be compromised.
- Future-proofing requires adopting quantum-safe cryptographic techniques, which are being actively researched by blockchain asset investments consultants and global digital asset consulting firms.
Grover’s Algorithm: Weakening Hash-Based Security
Grover’s Algorithm is designed to speed up unsorted database searches, which has significant implications for cryptographic hash functions.
How It Works:
- Classical computers take N steps to find a target value in an unsorted database.
- Grover’s Algorithm reduces this to roughly √N steps, doubling the speed at which hash-based security mechanisms could be compromised.
Impact on Hash-Based Cryptography (SHA-256):
- Many blockchain networks rely on SHA-256 hashing (e.g., Bitcoin mining).
- While Grover’s Algorithm alone does not render SHA-256 completely useless, it reduces its effective security strength from 256 bits to 128 bits, making brute-force attacks more feasible.
Mitigation Strategies:
- Researchers are exploring hash functions with larger output sizes and quantum-resistant hash functions such as SPHINCS+.
- Real-world DeFi investment consultants, crypto investment firms, and portfolio management consultants are evaluating these new cryptographic approaches to secure DeFi protocols.
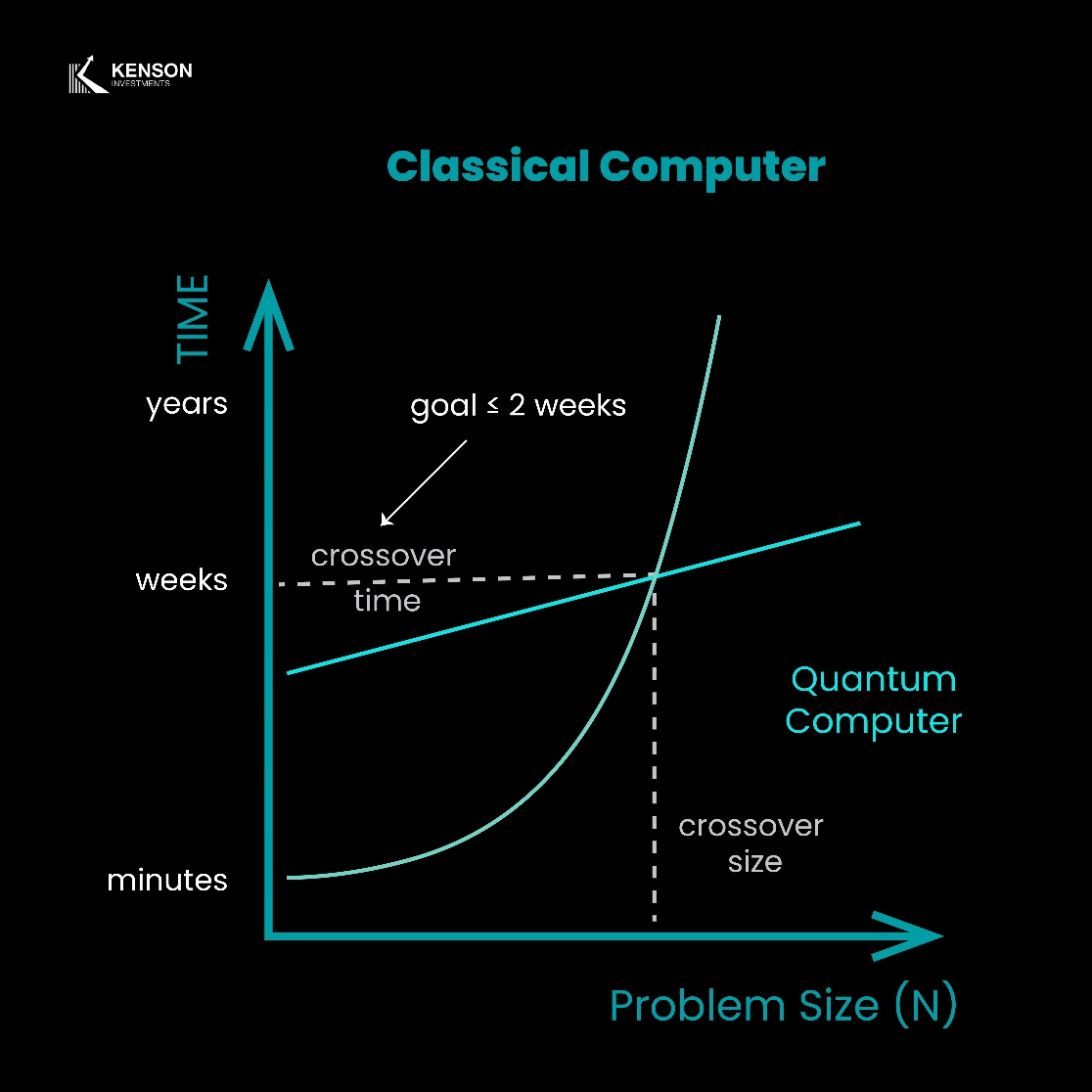
Why Classical Computers Are Limited
Classical computers, even with modern advancements in processing power, are fundamentally restricted by their binary processing nature. A classical computer attempting to factor a 2048-bit RSA key (which is standard for encryption today) would take an estimated 300 trillion years using brute-force methods. However, a powerful enough quantum computer could complete the same task in minutes to hours using Shor’s Algorithm.
With financial institutions and blockchain asset consulting firms relying heavily on cryptographic security, this speed advantage poses an existential threat to digital asset investment solutions and crypto investment firms that depend on encryption for asset protection.
The Quantum Computing Timeline: When Will the Threat Materialize?
Although quantum computing is still in its early stages, it is progressing rapidly. The table below highlights key milestones in quantum computing:
| Year | Milestone | Organization |
| 2019 | Google’s Sycamore quantum processor achieves quantum supremacy | |
| 2022 | IBM unveils a 433-qubit processor, pushing quantum computing scalability | IBM |
| 2025 | Forecasted emergence of 1000+ qubit quantum computers | Industry Projections |
| 2030 | Expected commercialization of large-scale quantum systems | Multiple Companies |
| 2035+ | Quantum computers capable of breaking RSA-2048 encryption | Research Estimates |
According to the U.S. National Institute of Standards and Technology (NIST), large-scale quantum computers capable of breaking current cryptographic standards may emerge within the next 10-15 years. This gives businesses, including digital asset consulting for compliance and DeFi finance consulting services, a limited window to transition toward quantum-resistant cryptography before threats become a reality.
The Threat to Blockchain and Digital Assets
As quantum computing advances, its ability to break traditional encryption standards threatens blockchain networks, decentralized finance (DeFi) platforms, and digital asset security. Current blockchain infrastructure relies on cryptographic algorithms that, while secure against classical computing, are vulnerable to quantum-powered attacks. If blockchain networks do not transition to quantum-resistant cryptographic solutions, digital assets could become exposed to unauthorized transactions, private key compromises, and system-wide breaches.
How Quantum Computing Threatens Blockchain Security
Blockchain networks rely on cryptographic functions to ensure security, trust, and immutability. Two fundamental cryptographic mechanisms form the backbone of blockchain technology:
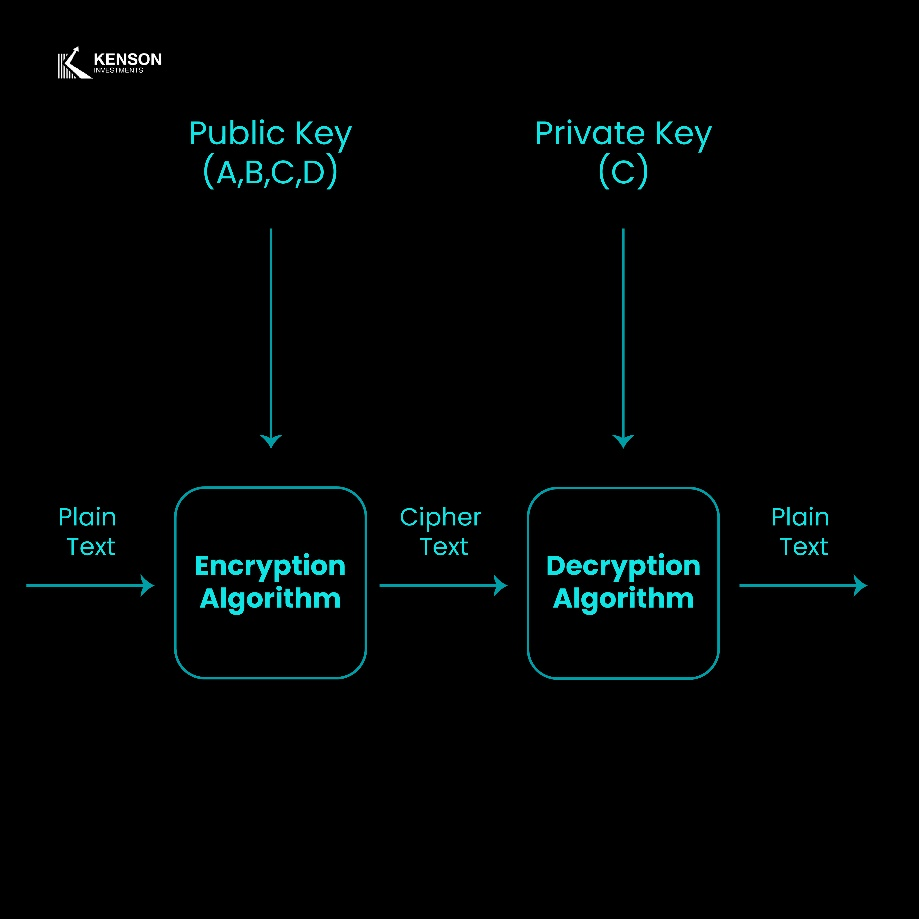
1. Public-Key Cryptography (Asymmetric Cryptography)
Public-key cryptography (PKC), also known as asymmetric cryptography, is a cornerstone of blockchain security. It is primarily used for digital signatures, ensuring that transactions are authenticated, verifiable, and resistant to tampering.
How It Works
Public-key cryptography uses a pair of keys:
- Public Key:A publicly available identifier that can be shared with others.
- Private Key:A confidential key known only to the owner, used to sign transactions and verify identity.
When a user initiates a transaction on a blockchain network, the transaction is signed using their private key. The network then verifies the transaction using the associated public key. If the signature is valid, the transaction is considered legitimate and is added to the blockchain.
Why Public-Key Cryptography is Essential for Blockchain
- Authentication:Ensures that transactions originate from legitimate users.
- Integrity:Prevents unauthorized modifications to transaction data.
- Non-Repudiation:Once a transaction is signed and recorded, the sender cannot deny having sent it.
Real-World Applications in Blockchain
- Bitcoin and Ethereum:Use the Elliptic Curve Digital Signature Algorithm (ECDSA) for transaction verification.
- Smart Contracts:Require digital signatures for executing self-executing agreements on platforms like Ethereum.
- Multi-Signature Wallets:Enhance security by requiring multiple private keys to authorize transactions.
Public-key cryptography is a foundational element explored by blockchain asset investments consultants, cryptocurrency investment consultants, and digital asset portfolio management firms for building secure DeFi platforms.
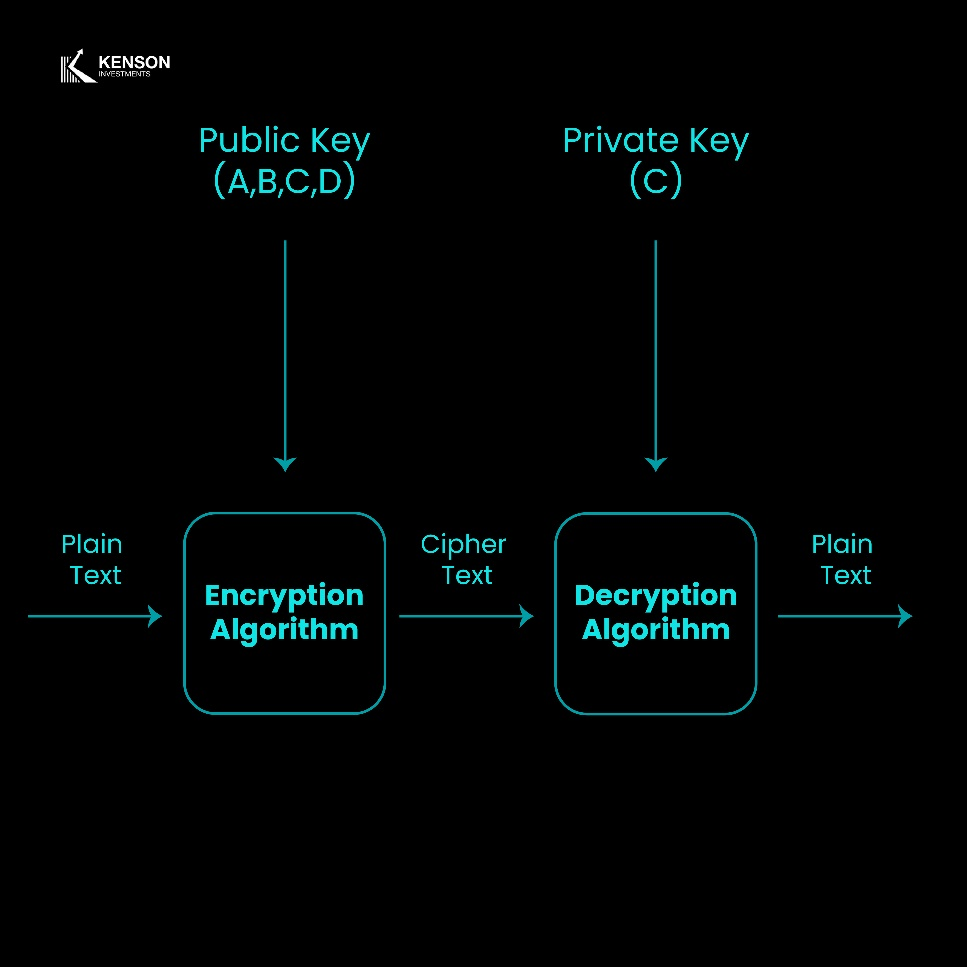
2. Cryptographic Hash Functions
Hash functions are another essential cryptographic tool that plays a crucial role in securing blockchain networks. They transform input data into a fixed-length string, known as a hash, which acts as a unique digital fingerprint of the original data.
How Hash Functions Work
A cryptographic hash function takes an input (such as a transaction or block of data) and produces an output of fixed size. Some of the key properties of a strong cryptographic hash function include:
- Deterministic:The same input always produces the same output.
- Fast Computation:The function must generate a hash efficiently.
- Preimage Resistance:It should be computationally infeasible to reverse-engineer the original input from its hash.
- Collision Resistance:Two different inputs should not produce the same hash value.
- Avalanche Effect:A small change in the input drastically changes the output.
Why Hash Functions Are Critical to Blockchain Security
- Securing Blocks in a Blockchain:Each block contains the hash of the previous block, creating a chain of interlinked data. If an attacker attempts to alter a past block, its hash will change, breaking the chain’s integrity.
- Proof of Work (PoW) and Proof of Stake (PoS):PoW-based networks like Bitcoin use hash functions (SHA-256) to validate mining efforts, while PoS networks use them to verify staking and block validation.
- Ensuring Data Integrity:Hash functions guarantee that blockchain data remains unchanged and tamper-proof.
Real-World Blockchain Applications
- Bitcoin:Uses SHA-256 for mining and block hashing.
- Ethereum:Uses Keccak-256 for transaction hashing and smart contract security.
- IPFS (InterPlanetary File System):Uses cryptographic hashes to identify and retrieve decentralized data.
Many crypto investment firms, real world assets on-chain investment consultants, and digital asset consulting firms focus on enhancing blockchain security through advanced cryptographic hash functions to ensure long-term resilience against cyber threats.
Quantum computers could disrupt both of these mechanisms in the following ways:
1. Breaking Public-Key Cryptography
- Bitcoin, Ethereum, and most blockchain networks use Elliptic Curve Digital Signature Algorithm (ECDSA) for securing transactions.
- A quantum computer running Shor’s Algorithm could compute private keys from public keys, allowing attackers to steal funds or alter transactions.
- Bitcoin’s blockchain currently protects addresses by not revealing public keys until funds are spent—but once a transaction is made, the public key is visible, making it vulnerable to quantum decryption.
A study by Deloitte estimates that a 10-million-qubit quantum computer could break Bitcoin’s encryption within minutes, potentially exposing billions of dollars in digital assets.
2. Weakening Hash Functions (SHA-256)
- SHA-256, the cryptographic function securing Bitcoin’s Proof-of-Work (PoW) system, relies on computational difficulty to prevent tampering.
- Grover’s Algorithm could cut the security strength of SHA-256 by half, making it easier to manipulate transactions.
- While this doesn’t immediately break blockchain security, it significantly reduces the time required for brute-force attacks.
If blockchain networks fail to upgrade their encryption, attackers could potentially modify transaction histories, counterfeit tokens, or compromise DeFi platforms. This is particularly concerning for blockchain asset investments consultants, DeFi finance consulting services, and digital asset strategy consulting firms, all of whom rely on secure cryptographic foundations.
Potential Quantum Attack Scenarios in DeFi and Crypto Markets
1. Private Key Exposure and Asset Theft
- A malicious actor with access to a quantum computer could extract private keys from public keys, gaining control over wallets and smart contracts.
- DeFi platforms, which store billions of dollars in locked assets, would be particularly vulnerable.
2. Smart Contract Manipulation
- Smart contracts rely on cryptographic proofs to execute agreements securely. If their encryption is compromised, attackers could alter contract terms or drain liquidity pools.
- Real world DeFi investment consultants and crypto investment firms must ensure that protocols transition to quantum-secure cryptography to mitigate such risks.
3. 51% Attacks and Blockchain Rewrites
- If an entity with quantum capabilities gains control over blockchain hashing power, they could manipulate the consensus mechanism, rewriting transaction history and double-spending tokens.
- This could disrupt entire crypto investment companies, hedge fund investment firms, and digital asset management services that depend on blockchain integrity.
According to a report by the Global Risk Institute, over 25% of cybersecurity professionals believe that quantum attacks on cryptocurrencies will be possible within 10 years.
Who is Most at Risk?
The most vulnerable segments of the crypto industry include:
- Bitcoin and Ethereum holders – Since these networks use ECDSA, quantum computers could expose their private keys.
- DeFi lending and staking platforms – Vulnerable smart contracts could be exploited if cryptographic protection weakens.
- Crypto exchanges and custodial services – If encryption protocols are compromised, user funds could be at risk.
- Institutions and hedge funds investing in digital assets – Firms relying on blockchain for investment analysis and portfolio management must assess the quantum-readiness of their holdings.
With real world assets on chain investment consultants and RWA tokenization investment consultants increasingly adopting blockchain solutions, addressing quantum risks is critical for maintaining trust and security in digital asset markets.
Post-Quantum Cryptography: Solutions for Securing Digital Assets
As the risk of quantum attacks becomes more imminent, blockchain networks, crypto investment companies, and digital asset management firms must proactively adopt quantum-resistant cryptographic solutions. The field of post-quantum cryptography (PQC) focuses on developing encryption methods that can withstand quantum computing attacks, ensuring the long-term security of digital asset investment solutions and blockchain-based financial systems.
What is Post-Quantum Cryptography (PQC)?
Post-quantum cryptography refers to cryptographic algorithms designed to be resistant to attacks from both classical and quantum computers. These algorithms rely on complex mathematical problems that quantum computers cannot easily solve, even with advanced computational power.
The U.S. National Institute of Standards and Technology (NIST) is currently leading an initiative to standardize quantum-resistant encryption algorithms, with an expected release of official standards by 2024–2025.
As the threat of quantum computing to traditional cryptographic systems looms, researchers and industry experts are actively exploring quantum-resistant encryption methods. Several cryptographic techniques have emerged as leading candidates for post-quantum security, each with unique strengths and challenges. These methods are at the forefront of discussions among digital asset strategy consulting firms, blockchain and digital asset consulting services, and RWA DeFi investment consultants aiming to ensure long-term security for digital assets.
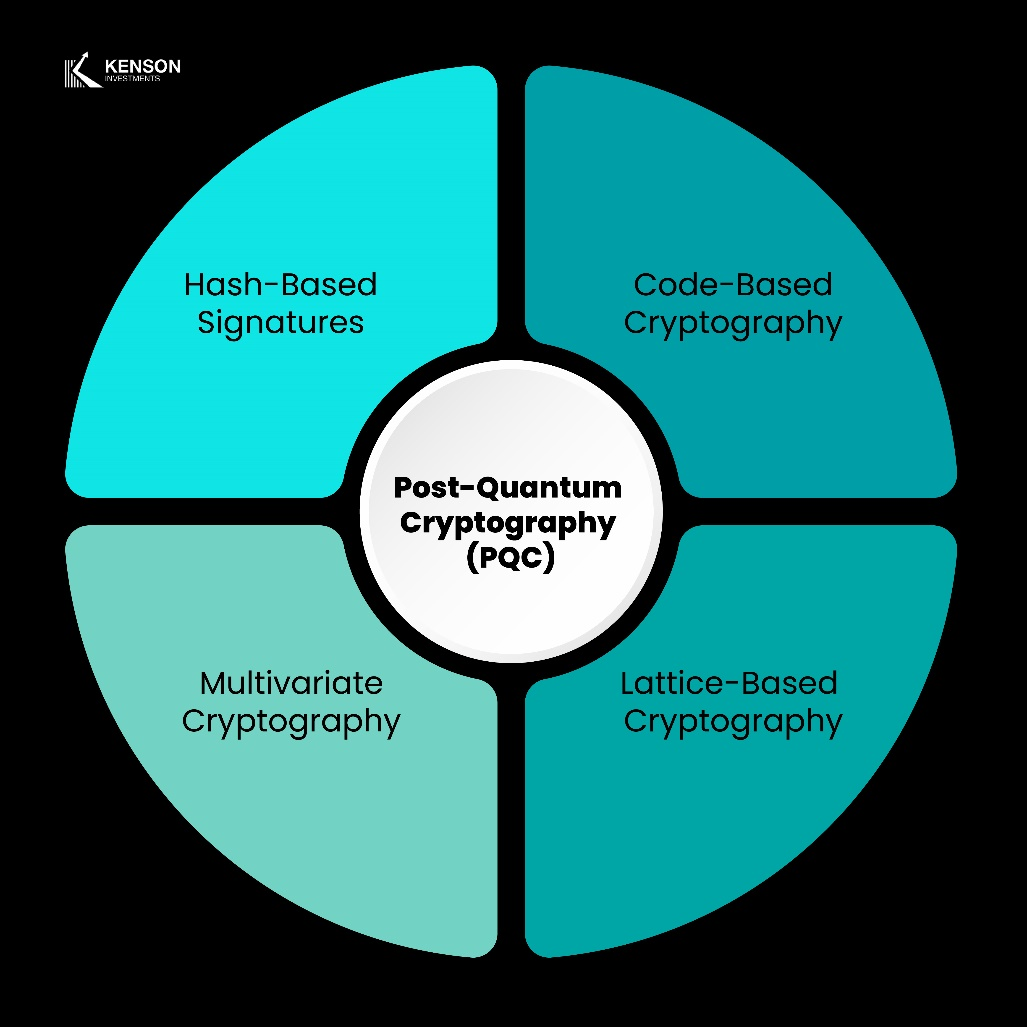
1. Lattice-Based Cryptography
Lattice-based cryptography is one of the most promising approaches to post-quantum security due to its strong resistance to both classical and quantum attacks. It relies on the inherent difficulty of solving mathematical problems related to high-dimensional lattices, such as:
- Learning With Errors (LWE):A problem where an attacker must determine a hidden vector given a noisy linear system—believed to be hard even for quantum computers.
- Shortest Vector Problem (SVP):Finding the shortest nonzero vector in a high-dimensional lattice, a problem considered infeasible to solve efficiently.
Why It’s a Leading Contender
Lattice-based cryptography offers several advantages:
- High Security:Even quantum computers struggle to solve lattice-based problems efficiently.
- Versatility:Can be applied to public-key encryption, digital signatures, and fully homomorphic encryption (FHE).
- Scalability:Provides fast encryption and decryption processes, making it viable for large-scale blockchain applications.
Examples of Lattice-Based Algorithms
- CRYSTALS-Kyber:A key encapsulation mechanism (KEM) selected by NIST for post-quantum encryption.
- NTRUEncrypt:A public-key encryption algorithm that relies on lattice structures for security.
- FHE-based Schemes:Allow computations on encrypted data, which could benefit secure blockchain transactions.
Lattice-based cryptography is already being integrated into research by digital asset consulting for compliance firms and blockchain asset investments consultants to fortify digital infrastructure against quantum attacks.
2. Multivariate Polynomial Cryptography
This technique is based on the computational difficulty of solving systems of multivariate quadratic equations over finite fields. Unlike traditional cryptographic schemes that rely on number theory, multivariate cryptography presents an alternative approach to post-quantum security.
How It Works
- The security of multivariate cryptographic systems relies on the fact that solving arbitrary multivariate quadratic equations is NP-hard.
- Even with quantum computing capabilities, no known efficient algorithms can solve these equations at a practical scale.
Advantages of Multivariate Cryptography
- Highly Efficient:Encryption and decryption processes are computationally light, making it suitable for resource-constrained environments.
- Proven Security:The core mathematical problem has been extensively studied and remains difficult for both classical and quantum computers.
- Flexible Applications:Used for digital signatures, authentication, and encryption.
Examples of Multivariate Cryptographic Algorithms
- Rainbow:A signature scheme based on multivariate quadratic equations that has been considered in NIST’s PQC standardization process.
- TTS (Tame Transformation Signatures):A variant designed for lightweight cryptographic operations.
Multivariate cryptography is being explored by cryptocurrency investment solutions providers and crypto investment firms for its potential in digital asset authentication and secure transactions.
3. Hash-Based Cryptography
Hash-based cryptography is one of the oldest and most well-understood cryptographic approaches. It uses cryptographic hash functions, which remain secure against quantum attacks because they do not rely on number-theoretic assumptions that Shor’s Algorithm can break.
Why Hash-Based Cryptography is Quantum-Resistant
- Shor’s Algorithm primarily affects public-key cryptography, but hash functions are not vulnerable to its attack model.
- Quantum computers can speed up brute-force attacks on hashes (via Grover’s Algorithm), but doubling hash length mitigates this risk.
Use Cases and Strengths
- Digital Signatures:Hash-based cryptographic signatures can be used to authenticate blockchain transactions.
- Data Integrity:Ensures tamper-proof data in decentralized finance (DeFi) and secure storage solutions.
- Longevity:Resistant to quantum computing advancements with minimal modifications.
Examples of Hash-Based Cryptographic Schemes
- Lamport Signatures:One-time digital signatures based on hash functions, providing strong post-quantum security.
- SPHINCS+:A stateless hash-based signature scheme being considered for post-quantum cryptography standards.
Many bitcoin investment consultants and digital asset management consultants are evaluating hash-based cryptography as a safeguard against quantum threats while ensuring blockchain integrity.
4. Code-Based Cryptography
Code-based cryptography is another post-quantum technique rooted in error-correcting codes. This method leverages the complexity of decoding randomly generated linear error-correcting codes, which remains a computationally difficult problem even for quantum computers.
How It Works
- Code-based encryption schemes use complex algebraic structures where only the private key holder can efficiently decode messages.
- Unlike RSA or ECC, there is no known quantum algorithm that significantly reduces the difficulty of these problems.
Advantages of Code-Based Cryptography
- Highly Secure:The McEliece cryptosystem, introduced in 1978, remains unbroken despite decades of research.
- Quantum-Resistant:Large key sizes enhance security against both classical and quantum attacks.
- Proven Reliability:McEliece encryption has been analyzed extensively and is considered one of the strongest quantum-resistant techniques.
Examples of Code-Based Cryptographic Algorithms
- McEliece Cryptosystem:Uses Goppa codes for encryption and has stood the test of time in cryptographic research.
- BIKE (Bit-Flipping Key Encapsulation):A new proposal for post-quantum key exchange.
Because code-based encryption requires large key sizes, its adoption in DeFi applications is still under evaluation by real asset tokenization investment consultants, digital asset consulting for startups aiming to balance security and efficiency.
How Blockchain Networks Are Adapting
To safeguard crypto asset management and digital asset consulting for startups, blockchain networks are taking proactive steps to integrate quantum-resistant cryptographic protocols.
1. Transitioning to Post-Quantum Signatures
- Ethereum is researching quantum-resistant alternatives to its Elliptic Curve Digital Signature Algorithm (ECDSA).
- Bitcoin developers are exploring Schnorr Signatures and Lattice-Based Cryptography as alternatives to ECDSA.
2. Hybrid Cryptographic Models
- Some blockchains are integrating both classical and quantum-resistant cryptography to maintain compatibility while ensuring security against future quantum threats.
- Projects like Quantum Resistant Ledger (QRL) are pioneering blockchain designs that use XMSS (Extended Merkle Signature Scheme) to protect transactions.
3. Upgrading Smart Contract Security
- DeFi platforms and real world assets crypto investment consultants are exploring quantum-safe smart contracts that use PQC signatures instead of traditional ECDSA verification.
- New security standards will help protect blockchain asset consulting firms and Stablecoin investment consultants from potential vulnerabilities.
4. Developing Quantum-Secure Consensus Mechanisms
- Traditional Proof-of-Work (PoW) and Proof-of-Stake (PoS) systems could be vulnerable to quantum computing.
- Quantum-resistant consensus models, such as Proof-of-Space-Time (PoST), offer alternatives to ensure long-term security for digital assets consulting firms and cryptocurrency investment consultants.
Proactive Measures for Investors and Institutions
For portfolio management and digital asset management, preparing for quantum threats is crucial. Investors and institutions should consider:
Adopting Quantum-Resistant Wallets
- Some hardware wallets and crypto investment firms are beginning to integrate PQC security.
- Look for wallets that support XMSS or lattice-based encryption.
Diversifying Digital Asset Holdings
- Institutions should ensure their portfolios include assets and protocols that are preparing for quantum-resistant upgrades.
- Stablecoins for investment, altcoin investment options, and real world asset consultants should assess projects based on future security measures.
Monitoring NIST’s Post-Quantum Cryptography Standards
- The final selection of quantum-safe algorithms by NIST will set the industry standard.
- RWA tokenization investment consultants and DeFi real world assets investment consultants should stay informed about regulatory updates and compliance requirements.
Engaging with Quantum-Secure Blockchain Projects
- Several blockchain startups are already implementing quantum-resistant encryption.
- Institutional investors should evaluate crypto investment firmsand digital asset management companies based on their preparedness for quantum risks.
Regulatory Perspectives on Quantum-Resistant Cryptography
As the risk of quantum threats grows, global regulatory bodies are beginning to assess the implications for digital asset management services, blockchain asset consulting, and crypto investment firms. Governments and financial institutions recognize that without proper regulation and standards, the transition to quantum-resistant encryption could be disorganized, leaving critical financial systems exposed.
Current Regulatory Landscape
Several organizations are actively working to set standards and guidelines for post-quantum cryptography:
1. National Institute of Standards and Technology (NIST)
- NIST is leading the Post-Quantum Cryptography Standardization Project, identifying encryption algorithms that can resist quantum computing attacks.
- By 2024–2025, NIST is expected to finalize and recommend quantum-resistant cryptographic standards for global adoption.
2. European Union Agency for Cybersecurity (ENISA)
- ENISA has published guidelines on quantum-safe cryptographic migration, urging digital asset management companies and financial institutions to prepare for post-quantum security risks.
3. Financial Action Task Force (FATF)
- FATF is working on compliance frameworks for digital assets consulting firms to ensure that DeFi platforms remain secure and legally compliant in a quantum-enabled world.
4. International Organization for Standardization (ISO)
- ISO is working on new cybersecurity frameworks, including ISO/IEC 14888, which aims to address digital asset consulting for compliance with quantum-resistant security standards.
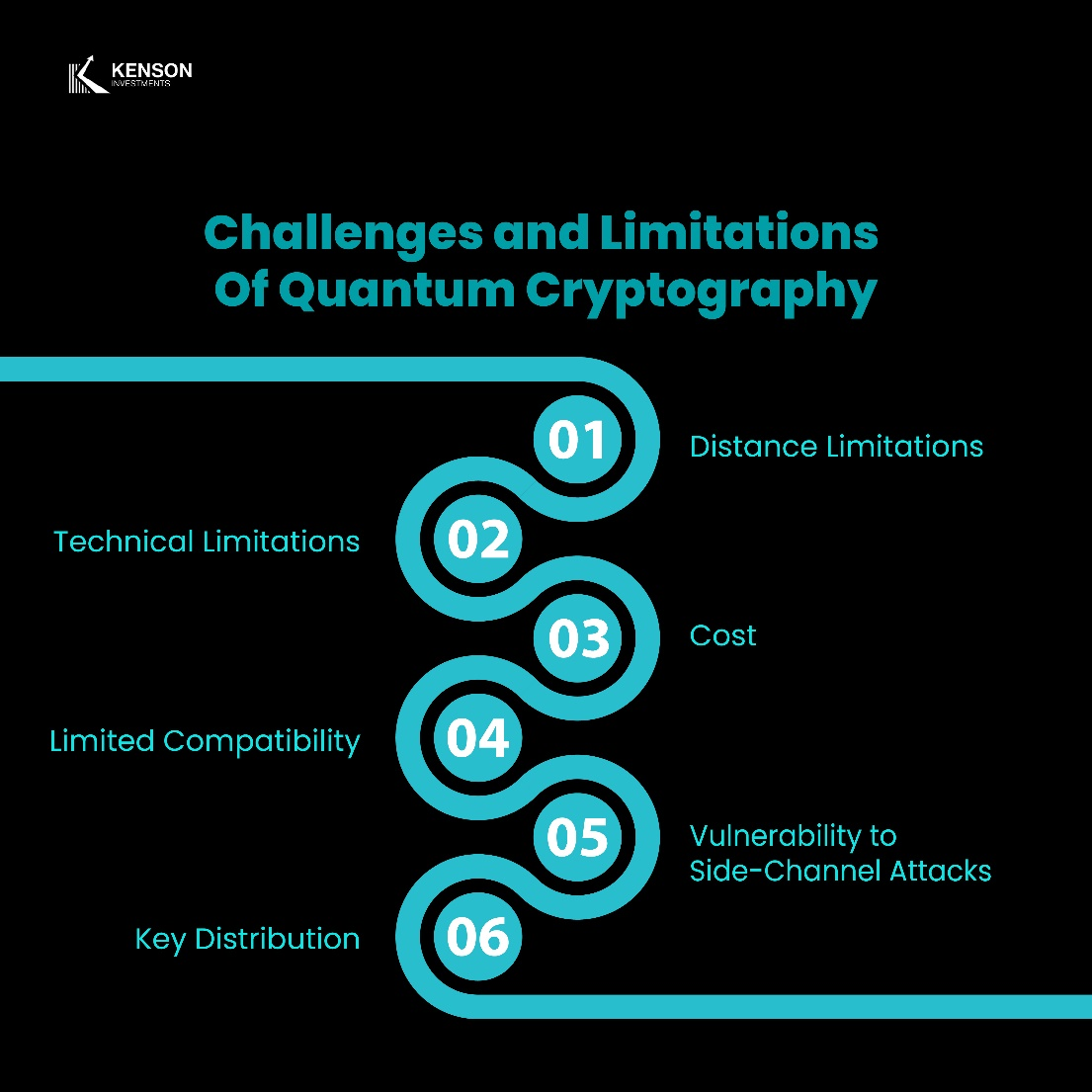
Regulatory Challenges in Quantum-Resistant Cryptography
Despite efforts to establish post-quantum security standards, regulators and industry leaders face significant challenges:
1. Lack of Immediate Threat Perception
- Some policymakers underestimate the near-term risks of quantum computing, delaying proactive regulations.
- Without clear mandates, hedge fund investment companies and real world assets crypto investment consultants may not prioritize security upgrades.
2. Standardization and Implementation Costs
- Transitioning from classical cryptography to post-quantum encryption requires significant investment.
- Many digital asset management firms may struggle to upgrade their security frameworks without industry-wide enforcement.
3. Interoperability Between Legacy and Quantum-Safe Systems
- Financial institutions must ensure that existing blockchain networks remain operational while integrating quantum-resistant cryptography.
- Global digital asset consulting firms are exploring hybrid security models that allow for gradual migration.
4. Compliance with Global Security Frameworks
- Many blockchain and digital asset consulting firms operate in multiple jurisdictions, making it difficult to comply with differing regulatory requirements.
- The lack of universal quantum security standards could create fragmentation in digital asset regulations.
Steps Governments and Institutions Are Taking
To mitigate these challenges, governments, financial institutions, and RWA DeFi investment consultants are taking proactive steps:
1. Mandating Quantum-Safe Standards for Financial Institutions
- Central banks and financial regulators in the U.S., EU, and China are developing quantum security guidelines for digital asset management companies.
- Some institutions are requiring crypto investment companies to assess their quantum security risks as part of compliance audits.
2. Funding Research into Quantum-Resistant Cryptography
- The U.S. government has allocated over $1.2 billion to quantum research initiatives under the National Quantum Initiative Act.
- The European Quantum Communication Infrastructure (EuroQCI) is investing in quantum-safe encryption technologies for digital asset investment solutions.
3. Encouraging Private Sector Collaboration
- Financial regulators are working with blockchain asset investments consultants to develop industry-wide best practices for quantum security.
- Crypto investment firms are collaborating with research institutions to test quantum-resistant encryption algorithms.
4. Developing Regulatory Sandboxes for Quantum-Safe Solutions
- Some governments are launching regulatory sandboxes to test quantum-resistant DeFi protocols before widespread implementation.
- DeFi real world assets investment consultant sare participating in pilot programs to evaluate security token investment strategies under post-quantum frameworks.
How Investors Can Prepare for Regulatory Changes
For cryptocurrency investment consultants, real world asset consultants, and digital asset portfolio management firms, staying ahead of regulatory developments is crucial. Key steps include:
Monitoring NIST and ISO Updates
- Regularly review NIST’s post-quantum cryptography standards and ISO cybersecurity guidelines.
- Security tokens investment consultants should ensure their portfolio management strategies align with upcoming compliance requirements.
Evaluating DeFi Protocols for Quantum-Safe Features
- Digital asset consulting for startups should assess whether blockchain projects are integrating quantum-resistant encryption.
- Projects with strong regulatory compliance measures may offer long-term security advantages.
Collaborating with Digital Asset Compliance Experts
- Engaging with digital asset consulting for compliance can help crypto asset management firms navigate evolving quantum security regulations.
- Ensuring regulatory alignment will be critical for institutions managing Stable coins for investment and altcoin investment options.
The Future of Quantum-Resistant Digital Asset Infrastructure
As the digital asset ecosystem braces for the era of quantum computing, blockchain developers, cybersecurity experts, and global digital asset consulting firms are working to future-proof financial infrastructure. The transition to quantum-resistant cryptography will not only safeguard crypto asset management platforms but also reshape how DeFi finance consulting services and investment analysis and portfolio management operate in a post-quantum world.
Emerging Solutions in Quantum-Resistant Blockchain Technology
To mitigate quantum threats, the industry is actively developing and testing security mechanisms that ensure blockchain networks remain immutable and resistant to advanced computational attacks.
1. Post-Quantum Cryptographic Algorithms
- NIST’s Post-Quantum Cryptography Standardization Project has narrowed down four primary algorithms for encryption and digital signatures:
- CRYSTALS-Kyber (Key encapsulation mechanism)
- CRYSTALS-Dilithium (Digital signatures)
- Falcon (Lattice-based cryptography)
- SPHINCS+ (Stateless hash-based signatures)
- These algorithms will be fundamental in upgrading blockchain asset investments consultant protocols and crypto investment firms for long-term security.
2. Quantum-Safe Blockchain Architectures
- Some digital asset investment solutions are exploring quantum-resistant ledgers based on lattice-based cryptography and hash-based cryptographic signatures.
- Projects like Quantum Resistant Ledger (QRL) and Vitalik Buterin’s Ethereum quantum research are investigating methods to upgrade Ethereum’s proof-of-stake (PoS) system with post-quantum cryptography.
- DeFi real world assets investment consultants are assessing the feasibility of integrating quantum-secure smart contracts into decentralized applications (dApps).
3. Hybrid Classical-Quantum Security Models
- To ensure a smooth transition, some real-world assets on-chain investment consultants are proposing hybrid models that combine current encryption standards with quantum-resistant cryptography.
- This strategy enables digital asset consulting for startups to integrate quantum-safe security without disrupting existing blockchain infrastructures.
4. Decentralized Key Management Solutions
- One of the biggest concerns for digital assets consulting firms is the security of private keys in a quantum-powered hacking environment.
- Solutions like distributed key generation (DKG) and multi-party computation (MPC) are being explored to protect user funds on DeFi platforms.
How DeFi and Digital Asset Management Will Adapt
The evolution of quantum-resistant cryptography will bring significant changes to blockchain and digital asset consulting, particularly in DeFi lending, staking, and investment solutions.
1. Enhanced Security for DeFi Lending and Borrowing
- Consultancy for DeFi finance investments will need to integrate quantum-resistant protocols into smart contracts to prevent unauthorized asset withdrawals.
- Stablecoin investment consultants are researching ways to ensure stablecoins remain secure against quantum-based decryption attacks.
2. Evolution of Digital Asset Custody Solutions
- Digital asset management companies will need to update cold storage solutions with quantum-resistant cryptographic standards.
- Portfolio management consultants are working on secure multi-signature wallets that can withstand quantum attacks.
3. Changes to Proof-of-Stake (PoS) and Proof-of-Work (PoW) Models
- Some altcoin investment options may require entirely new consensus mechanisms to avoid potential vulnerabilities.
- Companies investing in blockchain projects must evaluate whether the networks they support are implementing quantum-safe consensus protocols.
Challenges in Transitioning to Quantum-Resistant Blockchain Systems
While quantum-resistant encryption is promising, real world DeFi investment consultants and security tokens investment consultants must address critical obstacles before widespread adoption can occur.
1. Scalability and Performance Issues
- Quantum-resistant algorithms require more computational power than traditional cryptographic methods, which could slow down blockchain networks.
- Digital asset portfolio management firms must balance security with network efficiency.
2. Compatibility with Existing DeFi Protocols
- Many crypto investment companies operate on Ethereum, Binance Smart Chain, and Solana, which would require substantial upgrades to become quantum-resistant.
- Digital asset consulting for compliance firms are working to develop interoperable solutions that do not disrupt existing smart contract ecosystems.
3. Industry-Wide Coordination and Adoption
- Without industry-wide cooperation, fragmented quantum-resistant implementations could create inconsistent security standards across crypto investment firms.
- Real asset tokenization investment consultants are pushing for collaborative efforts between blockchain networks, cybersecurity firms, and regulatory bodies.
Next Steps for Investors and Institutions
The transition to quantum-resistant cryptography will affect cryptocurrency investments, DeFi users, and institutional investors alike. Here are key steps to prepare for the shift:
1. Stay Informed About Quantum Computing Developments
- Monitor research from Google’s Quantum AI, IBM Q Network, and MIT’s quantum computing department.
- Follow updates from NIST, ISO, and blockchain cybersecurity firms regarding quantum-safe encryption standards.
2. Evaluate Digital Asset Portfolios for Quantum Risks
- Crypto asset management firms should assess whether their blockchain investments are upgrading to quantum-resistant encryption.
- Investment analysis and portfolio management should incorporate quantum security risk assessments into decision-making processes.
3. Support Quantum-Safe DeFi Projects
- Investing in DeFi projects prioritizing quantum resistance may provide long-term security benefits.
- Real world assets crypto investment consultants should work with projects developing quantum-resistant tokenization solutions.
4. Engage with Digital Asset Security Experts
- Collaborate with digital asset consulting firms that specialize in quantum-safe security protocols.
- Security tokens investment consultants should explore regulated custody solutions designed to protect against quantum threats.
Prepare for the Future of Digital Asset Security
As quantum computing advances, staying informed is crucial. Explore emerging cryptographic solutions with Kenson Investments and navigate the evolving landscape of blockchain security. Learn more through the Kenson Investments app today!