Blockchain technology has revolutionized various industries by offering a secure and transparent way to record and manage data. At the heart of this revolution lies the concept of Blockchain Layer 1, the base layer upon which everything else is built. Security and consensus mechanisms are the cornerstones of Layer 1 networks, ensuring the integrity and reliability of the entire blockchain ecosystem. This blog dives deep into these crucial mechanisms, exploring how they work and their impact on the security of digital assets.

The Importance of Layer 1 Security and Consensus
Imagine a public ledger where everyone can see the transactions, but no one can tamper with them. That’s the essence of a secure blockchain network. Layer 1 security ensures that transactions are irreversible and verifiable, fostering trust in the network. This is critical for various applications built on top of the blockchain, including cryptocurrencies, DeFi (Decentralized Finance), and NFTs (Non-Fungible Tokens).
For investors, particularly those involved with hedge fund company performance analysis, understanding Layer 1 security is essential when evaluating blockchain-based investment opportunities. Hedge fund companies exploring ethical investing strategies can leverage secure Layer 1 networks to ensure transparency and responsible investment practices. Cryptocurrency investment consultants can utilize their knowledge of Layer 1 security to guide clients through the complexities of Altcoins vs. major cryptocurrencies and other investment options (Crypto asset investment consultant, Investing in cryptocurrencies).
Now, let’s explore the two major consensus mechanisms that underpin Layer 1 security:
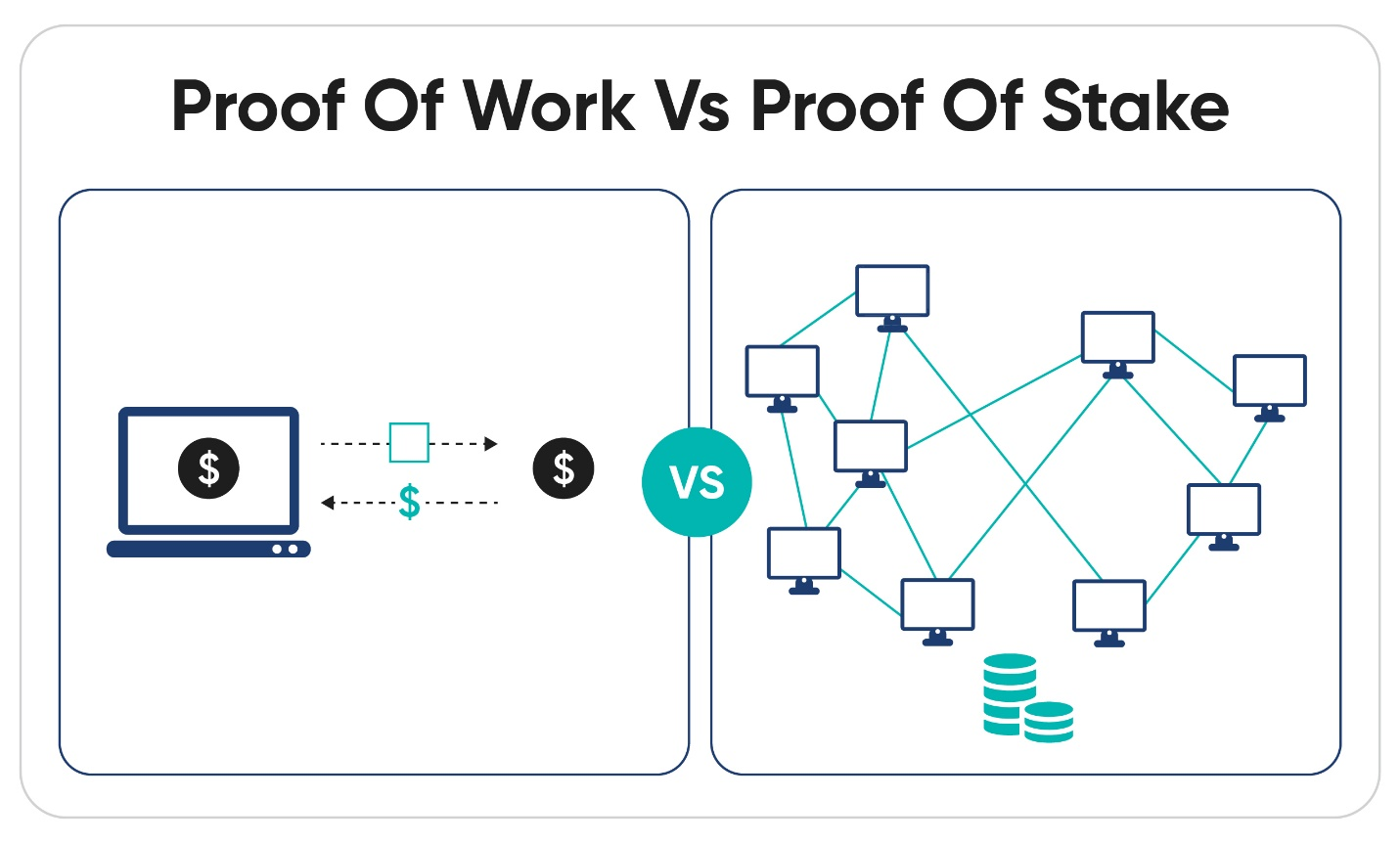
Proof-of-Work (PoW)
Proof-of-Work (PoW) is the original and most well-known consensus mechanism used by pioneering blockchains like Bitcoin. It was first introduced by Satoshi Nakamoto in the Bitcoin whitepaper published in 2008. This consensus mechanism plays a crucial role in ensuring the security and integrity of the blockchain network by making it computationally difficult to alter transaction history.
How Proof-of-Work (PoW) Works
Mathematical Problems
Miners in a PoW system compete to solve complex mathematical problems, also known as cryptographic puzzles. These problems require significant computational power to solve and are based on cryptographic hash functions. The difficulty of these problems adjusts periodically to ensure that new blocks are added to the blockchain at a consistent rate, approximately every 10 minutes in the case of Bitcoin.
Mining Process
Miners use specialized hardware, known as ASICs (Application-Specific Integrated Circuits), to perform a large number of calculations per second. The goal is to find a nonce (a random number) that, when combined with the block’s data and passed through the hash function, produces a hash value that meets the network’s difficulty target. This target is a number that the resulting hash must be lower than or equal to.

Validation and Block Addition
The first miner to solve the cryptographic puzzle and find a valid nonce broadcasts the solution to the network. Other nodes in the network then verify the solution to ensure it is correct. If the solution is valid, the miner earns the right to validate the block of transactions and add it to the blockchain. This process is known as “mining” the block.
Block Reward
As a reward for their work, the successful miner receives a block reward, which consists of newly created cryptocurrency and any transaction fees included in the block. This reward incentivizes miners to continue securing the network. For Bitcoin, the block reward is halved approximately every four years in an event known as the “halving,” reducing the rate at which new bitcoins are generated.
Security benefits of PoW:
High computational cost: Solving complex puzzles requires significant computing power, making it expensive and impractical for malicious actors to attempt a 51% attack (gaining control of the network).
Immutability: Once a block is added to the blockchain, it becomes incredibly difficult to alter due to the subsequent blocks referencing it.
Challenges of PoW
Energy consumption: Solving PoW puzzles requires a lot of processing power, leading to high energy consumption.
Scalability: As the network grows and transaction volume increases, validating transactions through PoW can become slow and expensive.
Proof-of-Stake (PoS)
Proof-of-Stake (PoS) is a newer consensus mechanism designed to address the limitations and inefficiencies of Proof-of-Work (PoW). It aims to provide a more sustainable and scalable solution for blockchain networks while maintaining security and decentralization. PoS is used by various blockchain platforms, including Ethereum 2.0, Cardano, and Tezos. Here’s a detailed look at how Proof-of-Stake works and its implications:
Core Concept of Proof-of-Stake (PoS)
Selection of Validators
In a PoS system, validators are chosen to create new blocks and validate transactions based on the amount of cryptocurrency they hold and are willing to “stake” or lock up as collateral. This stake acts as a security deposit that can be forfeited if the validator acts maliciously.
Probability of Selection
The likelihood of being chosen as a validator is proportional to the amount of cryptocurrency staked. For instance, if a validator holds 1% of the total staked cryptocurrency in the network, they have a 1% chance of being selected to validate the next block. This approach ensures that those with a higher stake have a greater incentive to maintain the network’s integrity.
Detailed Mechanics of Proof-of-Stake
Staking Process
To become a validator, a participant must deposit a specific amount of cryptocurrency into the network’s staking mechanism. This staked amount is locked up and cannot be used for transactions during the staking period.
Block Validation
When a new block is to be added to the blockchain, the network randomly selects a validator based on their stake. This validator is responsible for verifying the transactions in the block, ensuring their validity, and adding the block to the blockchain.
Rewards and Penalties
Validators receive rewards for their participation in the form of transaction fees and, in some cases, newly minted cryptocurrency. However, if a validator is found to act maliciously or fails to validate transactions properly, they can lose a portion or all of their staked cryptocurrency. This penalty mechanism, known as “slashing,” deters dishonest behavior and maintains network security.
Security benefits of PoS:
Lower energy consumption: PoS doesn’t require the same level of computational power as PoW, resulting in a significantly lower environmental impact.
Improved scalability: PoS networks can typically process transactions faster and more efficiently compared to PoW networks.
Challenges of PoS
Centralization concerns: If a small group of validators holds a large portion of the staked coins, it could potentially compromise the network’s decentralization.
Security risks: PoS networks are still relatively new, and their long-term security needs to be proven through continuous testing and development.
Other Consensus Mechanisms
Beyond PoW and PoS, several other consensus mechanisms are emerging, each with its own advantages and disadvantages. Here are a few examples:
Delegated Proof-of-Stake (DPoS): Similar to PoS, users vote for delegates to validate transactions.
Byzantine Fault Tolerance (BFT): Offers high fault tolerance but can be computationally expensive.
The choice of consensus mechanism for a Layer 1 network depends on various factors, including the desired level of security, scalability, and decentralization.
Navigating the Evolving Landscape with Kenson Investments
The world of blockchain technology is constantly evolving, with new innovations and consensus mechanisms emerging all the time. Staying informed about these advancements is crucial for investors seeking to navigate the digital asset market.
Kenson Investments is a leading investment firm dedicated to helping clients explore innovative investment solutions. We leverage our expertise in digital asset investments and blockchain asset investment consultant services to provide clients with comprehensive guidance on navigating the exciting world.
Get in touch with us today.